- Krakow-based Secfense is looking for Series Seed funding, after securing 700,000 euro in 2018
- The startup is a security “broker”, allowing its customers to deploy any secure login solution available on the market without changing the code of existing apps
- The company wants to expand its regional presence, starting with the UK
- Secfense is one of the finalists of UiPath’s 2020 Automation Awards
Krakow-based security startup Secfense, which aims to redefine the new default for strong user authentication, is looking for new capital to set up a branch in the United Kingdom.
“We are looking to raise our next funding round in Series Seed / Series AA, which will allow us to expand our sales activity abroad and register our company in the UK, which is our next sales destination”, Tomasz Kowalski, the company’s CEO and co-founder, told ITKeyMedia.
Series Seed or Series AA can be considered preliminary funding, usually to support less capital-intensive business growth. They come after the initial seed round and before a proper Series A.
Secfense’s pre-seed and seed rounds took place in 2018, when the startup raised 700,000 EUR from startup accelerator Bitspiration Booster, co-founded by ex-Google employees who established the Google R&D Center in Krakow (Paulina Mazurek and Wojtek Burkot), as well the co-founder of ASPIRE (Oskar Grzegorczyk) and the founder of Eventory, PLNOG, and CONFidence (Andrzej Targosz).
Based on preliminary projections, Secfense anticipates they would reach their first million euro (as ARR – Annual Recurring Revenue – editors’ note) “within the next three years”, says Kowalski.
Glossary
Before we get in the specifics of IT security solutions, a short intro or refresher on the basics:
2FA = Two-Factor Authentication = a subset of MFA (Multi-Factor Authentication), essentially an extra layer of security used to make sure that people trying to gain access to a protected resource truly are who they say they are. After the user inputs their (user)name and a password, they will be prompted to provide another piece of information, which might be:
- Something they know: PIN code/ authentication code, secondary password, answers to “secret questions”, etc.;
- Something they have: key, smart card, smartphone, hardware [USB] token, etc.;
- Something they are: usually biometrics (fingerprint/ iris scan, voice, pattern in key press intervals, etc.);
- Somewhere they are: connection to a specific network, GPS location, etc.
A potential compromise of one of the factors will not unlock access to the protected resource. So even if your password is stolen or your phone is lost, the chances of someone else having the second-factor information is unlikely.
- SMS (text message): you receive a code on your mobile device; you’ve probably seen it in most banking applications;
- One-Time Password (OTP): similar to SMS, but the code is generated on dedicated devices;
- Push-based: you must confirm the login on your smartphone via a dedicated app;
- Universal 2nd Factor (U2F): a dedicated USB token will verify your physical presence and identity;
- FIDO2 or WebAuthn: considered one of the safest solutions available on the market; Fast IDentity Online/ FIDO2 can use any local devices with biometric authentication (fingerprint reader on smartphone or laptop for example); WebAuthn is the standard allows those local authenticators to be used instead of passwords.
What Does Secfense Do Exactly?
Marcin Szary, co-founder and CTO of Secfense, says their solution can add any 2FA or MFA method to any application, without touching the code of the application in question, and scale it across the client’s entire organisation. “We are approaching an old problem (of strong authentication) in a different way. Most companies use password protection, some of them use tokens or MFA. We take it a step further and deliver a full package of strong authentication methods in minutes – we are a MFA enabler, meaning our solution allows deploying every MFA method available on the market”, he adds.
Traditionally, enabling MFA requires at least updating part of the source code of the target application, if not redesigning it. If a corporation has multiple critical applications/ systems, the complexity rises exponentially.
Secfense comes in and looks at the same problem not from a software development perspective, but rather from the point of view of the network. “We shift the paradigm of 2FA implementation (…) Instead of tying each app individually to the selected 2FA method, which is time- and money-consuming and requires development effort, you just reroute the web traffic through our proxy – which is as simple as changing a DNS entry or a firewall rule”, explains Szary.
We are not a multi-factor authentication provider. We are a multi-factor authentication broker.
— Marcin Szary, CTO and co-founder of Secfense
Considering the already saturated MFA solutions market, Secfense’s CTO says they made a strategic decision not to compete with them, at least not directly. “We keep repeating it like a mantra, but it is really important. We are not a multi-factor authentication provider. We are a multi-factor authentication broker (or an enabler)”, stresses Szary.
Kowalski complements: “The natural question is: will the client need to pay for the MFA solution and for the Secfense broker? There are free authentication standards (like authenticator apps, SMS-based OTPs, FIDO2-based local authenticators), and there are also authentication devices that need to be purchased (YubiKeys, Feitian keys, etc.). It is for our customers to decide which method they would like to use.”
From a semi-technical perspective, Secfense will sit somewhere on the network, learn traffic patterns related to authentication and add an additional security layer between users and their applications. “The broker knows which app the user wants to access, and it asks them to apply the 2FA method that was chosen for that specific app”, explains Szary.
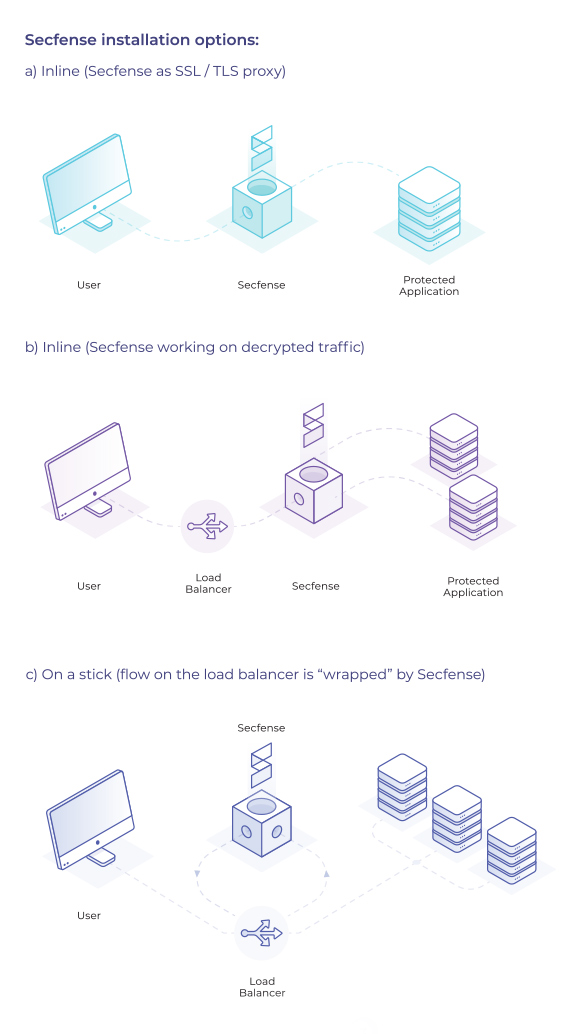
Three installation options available for Secfense
Taking it a step further, in 2019 Secfense rolled out microauthorisations, a feature that allows for a more granular protection, by requesting the user to reauthenticate each time they access a certain area or want to perform a specific task within the protected application.
Using the banking example from the beginning of the article, even after logging in, you would still have to input a separate authorisation code for each transaction. Why would such an apparently paranoid system be put in place? To diminish the risk of compromising sensitive data or performing unauthorised operations. An employee with enough access privileges could compromise an entire company, whether it is done on purpose or not; and, according to industry data, 34% of cyber attacks are internal.

▶ How microauthorisations work
Pricing Model and Clients
Secfense charges their clients an annual subscription fee per user, plus a one-time installation fee. The solution is not SaaS (Software as a Service) though; due to the sensitive nature of the data flowing through the app, most of their customers prefer on-premise deployments, but the startup is considering extending its offering to SaaS. The company did not offer any information about starting prices.
Secfense has six customers at the moment and three more are sales-ready, says Kowalski, adding that the company has done a bit over 20 proofs of concept (PoC) – which means a conversion rate of almost 30%. “Our customers are mainly financial institutions, but also large organisations from the public sector, as well as transportation and e-commerce verticals”, explains Secfense’s CEO.
He says the pandemic triggered a much higher interest in the startup’s solution:
Before March 2020, it was mainly outbound marketing and sales, with us reaching out to new customers. Since COVID, the situation has changed. This is all related to the necessity of maintaining a high level of security for remote employees working from home from unprotected networks.
— Tomasz Kowalski, CEO and co-founder of Secfense
Secfense was granted 800,000 PLN and 1,600,000 PLN (approximately 536,000 EUR in total) by the EU/ European Regional Development Fund, for a couple of projects that ran under the Smart Growth Operational Programme 2014-2020 and foresee the development and implementation of 2FA/ MFA methods that function independently of the protected applications in the infrastructure of potential customers.
Two Thirds of the Team Is Working Remotely
Secfense was established in March 2018 and currently has a team of 9 people, out of which 3 are working in the startup headquarters in Poland and the rest remotely.
The company’s founders each have almost 20 years of experience in the IT field and have crossed paths professionally multiple times since they first met in 2003.
CEO Tomasz Kowalski was involved in many hardware and software implementations in large and medium-sized companies from the finance, telco, and military sectors. The largest part of his career was spent in Polcom, as telco and media sales manager.
Marcin Szary is Secfense’s CTO, responsible for product development. His technical experience focused on security and identity management. Before Secfense, Szary was technical manager/ CTO for multiple startups in the mobile, telco, and security segments.
Note: Secfense is not to be confused with Secfence, an Indian company specialising in other cyber security solutions such as red teaming platforms, vulnerability and exploit research, cyber deception platforms.
A Deeper Dive into Cyber Security
In the following video, Secfense’s co-founders demo how to add 2FA on top of amazon.com:

▶ Adding two-factor authentication to amazon.com
Well! The use of technologies, procedures, and controls to defend against cyberattacks on systems, networks, programs, devices, and data is known as cyber security. By doing so, it hopes to lower the risk of cyberattacks and safeguard against unauthorized use of technologies, networks, and systems. Individuals’ addresses, bank account information, and other personal information are frequently altered and compromised. In response to this, a number of identity access management systems have been developed, allowing users to store all of their digital assets in a single location that is secure from cybercriminals looking to profit from any available opportunity.
When it comes to bigger cyber control, that is for the big companies, obviously Secfense does not have access to Amazon’s infrastructure, so how did they implement 2FA? Just by changing a DNS entry, to make traffic flow through their network, which is not a problem, since they have full control of the laptop used in the demo. DNS is basically a phonebook for the internet, it translates domain names to the numerical IP address needed for locating the servers that host the websites. For example, if you type http://172.217.22.164/ in your browser, you will get google.com.
But Secfense’s demo raises the question: “Does Secfense use a man-in-the-middle attack to intercept authentication requests?” – essentially yes, but the objective here is not to steal credentials, rather to insert an additional layer of security. As long as the client controls the DNS of the application they want to protect, Secfense can be deployed for those applications.
Secfense’s team have proposed a couple of analogies for this scenario:
- “Think of the Secfense security broker as Cloudflare for 2FA”, and
- “What Secfense did to 2FA is what VMware has done to infrastructure”.
Secfense is one of the finalists of the UiPath Automation Awards 2020.
The Romanian-born leading enterprise Robotic Process Automation (RPA) software company is looking to support the development of innovative business ideas in Central and Eastern Europe (CEE) and Turkey.
“A few years ago, UiPath was a start-up. So, we get you! We encountered many of the struggles and the perks that come along with the entrepreneurial journey”, say UiPath’s representatives.

▶ 2020 UiPath Automation Awards Showcase
There are 2 separate tracks, as UiPath will be awarding prizes for startups and for scaleups.
Secfense is nominated in the startup category and could win:
- Cash: 50,000 EUR, offered by Microsoft;
- Mentoring: Director-level mentors, 18 hours over 12 months;
- Tech support: 12 months access to UiPath developers; free licensing of UiPath technology for 12 months;
- Sales and marketing: access to marketing experts (30 hours over 12 months); featured presenter at UiPath Meetups; featured speaker at regional events/ hackathons/ developer conferences; featured subject on the UiPath Blog; invitations to showcase their solution at UiPath events.
The finalists will present their pitch on 17 December 2020, from 15:30 to 17:40 CET. Secfense is competing with Attention Insight from Lithuania and Neurolabs from Romania.
“I feel this year’s finalists are all great and, although I do have my favorites, I prefer not to name them”, Ondrej Bartos from Credo Ventures told ITKeyMedia when asked who would have what it takes to win.
What I’m convinced about is that all the finalists have already proven that their products and tech are interesting and stand out against many competitors in their verticals. If they have what it takes to win… we’ll just have to wait and see.
— Ondrej Bartos, general partner of Credo Ventures
This year, the UiPath Automation Awards are part of the company’s Reboot Work Festival. By signing up for the awards ceremony, you can also attend the entire 3-day festival for free.
Kowalski says the Secfense team found out about the competition through the F6S portal and decided to take their chances because automation is a big part of what their product brings to the table. “The three key values of our product are independence, flexibility, and scalability of strong authentication”.
He feels winning the competition will grant the company exposure and possibly open the doors to investors and clients. “Being able to use UiPath’s expertise, which also started as a couple-person startup, will help us avoid lots of early-stage mistakes that we wouldn’t be able to foresee otherwise”, concludes Kowalski.
And here is Secfense’s short video message before the big day, delivered by CTO Marcin Szary:

Sabin Popescu works as content editor, web designer/ developer and occasionally graphic designer for various companies and institutions across Eastern Europe and was an IT journalist for Romania’s leading business daily, Ziarul Financiar.